Computer Safety Tips
Money has become the primary motivation for attacking computers. At first, there were only malcontents, who sought to damage or deface websites and personal computers. Now, professional hackers are out to steal money from unsuspecting victims online. They have also learned to use technology that makes it relatively easy. Spam has also moved from intrusive cyber-marketing to outright scams such as phishing.
Anyone can contract a virus or worm that may make your computer not function properly. They have been eclipsed by things like spyware and Trojans though. Now you can loose small or large amounts of money, or even your financial identity.
Malicious software, known collectively as malware, is one of the primary hazards on the Internet. Deception, otherwise known as the "human engineering" aspect is the other.
The following descriptions have been presented here to give our users a basic understanding of the online threats that present a risk to computer systems. Understanding the dangers that exist online is the first step in developing intelligent users that will use the internet with security awareness.
- Virus - a self-replicating computer program written to alter the way a computer operates, without the permission or knowledge of the user. Viruses can be intentionally destructive (destroying sensitive information) or simply annoying. True viruses replicate and execute by themselves. There are several types of viruses which include boot sector virus, macro virus, logic bomb, time bomb, polymorphic, and stealth.
- Malware - refers to a broad range of software designed to damage or infiltrate computer systems. This includes spyware, adware, Trojan horses, worms and viruses.
- Spyware - in simplest terms is designed to collect information from users. Often these programs track what type websites are visited and sends this information to an advertising agency for marketing purposes. Some versions of spyware are malicious in nature that designed to record what a user types to obtain passwords and credit card information while others versions simply launch pop-up advertisements.
- Adware - also known as advertising-supported software is any software designed to automatically play, display or download advertising material in conjunction with other software that has been installed or while an application is being used. Adware often takes on the form of spyware (user's activity is tracked, reported, and often re-sold, often without the knowledge or consent of the user) or even malware (interfere with the function of other software applications, in order to force users to visit a particular web site).
- Trojan horse - is a very destructive program that masquerades as a benign application. Unlike viruses, Trojan horse programs do not replicate themselves. Hackers usually hide Trojan horses in games, small programs and even through email downloads that unsuspecting users then execute on their computers. There are several types of Trojan horse programs the worst of which enable hackers full control over a users computer through a remote computer.
- Worm - A program or algorithm that replicates itself over a computer network and usually performs malicious actions, such as using up the computer's resources and possibly shutting the system down. Worms spread from computer to computer, but unlike a virus, it has the capability to travel without any help from a person.
- Browser Hijacking - A browser hijacker (sometimes called hijackware) is a type of malware program that alters your computer's browser settings so that you are redirected to Web sites that you had no intention of visiting. Most browser hijackers alter default home pages and search pages to those of their customers, who pay for that service because of the traffic it generates. More virulent versions often: add bookmarks for pornographic Web sites to the users' own bookmark collection; generate pornographic pop-up windows faster than the user can click them shut; and redirect users to pornographic sites.
- Spam - is the abuse of electronic messaging systems to send unsolicited, undesired bulk messages. While the most widely recognized form of spam is e-mail spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, and mobile phone messaging spam.
- Phishing - emails to clients pretending to be from a trusted company asking for personal account information. These emails use realistic logos and images that appear to be from a trusted company such as your bank. They often ask for personal information and/or have a link that brings you to a fraudulently created site.
How to spot a Fraudulent Website:
Fraudsters have become increasingly sophisticated in their attempts to collect personal account information from users. Learn to spot a fraudulent website using these guidelines:
- Minimize the page - Fraudsters often use a pop-up box with an image of the correct URL directly on top of the real URL to fool users into thinking the page is authentic. If the address bar moves up or down when you minimize the page the site is a fake.
- Check the URL - Sometimes fraudsters create a copy of an authentic website but use a different URL. Always be sure a site's URL is authentic when visiting a site via a link. If you are not sure if a site's URL is authentic, type it in yourself.
- Be wary of pop-ups - Fraudsters will sometimes create a pop-up box that appears on top of a genuine site asking for personal account information. In this case, a fraudster has created a pop-up box that appears on top of a visa site.
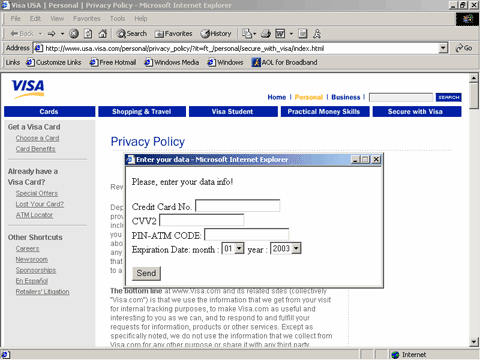
Trusted institutions will never ask for your PIN online- never enter personal information into these boxes. Pop-up blockers can help prevent these boxes from appearing.
Good Password Practices:
- Trusted institutions will never ask for your PIN online- never enter personal information into these boxes. Pop-up blockers can help prevent these boxes from appearing.
Good Password Practices: - Make your password at least eight characters in length.
- Include at least one character from each of the following three character groups:
- Upper case alphabetic characters (A-Z),
- Lower case alphabetic characters (a-z),
- Numbers and symbols ( 0-9~`!@#$%^&*()_-+={}[]|\:;"<>',.?/ )
- Please note: Passwords may not include blank spaces or control characters, such as return, tab, etc.
- Embed at least one number or symbol within the password rather than adding it to the beginning or end of an otherwise alphabetic string.
- Do NOT make your password a dictionary word or common name with numbers and symbols merely substituting for similar looking alphabetic characters (e.g., "P@ssw0rd").
- Remember to change your password regularly. This practice limits the amount of time that someone can use to guess your password and the amount of time that your password can be used if it is uncovered.
Measures you can take to reduce the risk of online threats:
- Never download software from a third party and/or unreliable source
- Ensure your operating system has the lasted security updates
- Scan your computer with various anti-virus software atleast once a week
- Always check for updates for your anti-virus software before scanning
- Never open email attachments from anyone you don’t know
- Back-up important data on a regular basis
- Never share personal or confidential information such as passwords
- Use your own intuition and good judgment before visiting websites
Already have an anti-virus solution?
In some cases anti-virus software, in an effort to keep your computer secure, will slow down a computers performance dramatically and constantly bombard a user with messages to confirm the use of programs and processes. Most users find this more of a nuisance if anything else and will often discard these messages and in some cases disable the anti-virus software. Remember, there is no ‘all in one’ anti-virus solution. It is the combination of different software, user awareness and intelligent decisions that enables users to be online without having to worry about their computer becoming infected. MIB Computers Tune-up Service covers all aspects of you computers security and performance. Our unique tune-up service is based on dozens of industry standard computer security books and countless hours of research. In addition to dozens of specialized security configuration adjustments and tweaks MIB Computers Tune-up Service gives users the best tools and programs available – all of which have been tested to ensure a healthy balance between computer performance and computer security.
For more information, comments or questions contact MIB Computers at 905-841-5105.
